How to avoid scams with CoinScan
Introduction:
How to avoid coin scams with CoinScan
CoinScan is committed to its mission of creating a safer and fairer environment for everyone within the cryptocurrency space. It is for this very reason that we have created some of the most comprehensive and pioneering scam-prevention tools on the market. Throughout this article we will take a deep dive into the scams themselves and how individuals can use CoinScan's various features – as well as general best practices they can employ – to help limit their exposure to fraudulent activity.
As a general rule, the frequency an individual encounters scam coins varies greatly depending on their particular trading style. Larger market cap cryptocurrencies tend to represent lower ROI trading opportunities but are considered safe (such as Ethereum and Dogecoin for example). Of course, there are always exceptions to this rule, as seen with projects such as Axie Infinity and Luna that both suffered sudden market crashes, the latter irrevocably. Conversely, new and unproven tokens can often represent far higher instant earning opportunities, but also carry an exponentially higher scam risk.
A lot of confusing ‘slang’ language is often used in the crypto space, so to make things simpler we have attached a glossary – which we will be using going forward and exploring in greater depth.
Definitions
Rug-Pull: This is a common scam where the token’s developer uses exploits within the contract to steal the funds of investors – either over time or all at once. There are various ways in which this can be done.
Remove Liquidity: When a developer removes the liquidity from a token, it immediately prevents the method used to trade, rendering everyone’s holdings worthless. The creator then steals the funds that are held in the liquidity pool.
Airdrop: The act of manually or automatically “sending” tokens to an address, primarily by a token’s deployer wallet. This is typically done before a token goes live (if there was a presale), and less commonly sometimes after a token is live.
Deployer: A token deployer is also commonly referred to as its developer. The ‘deployer’ is the wallet that created and launched a token onto the blockchain. Malicious developers will often deploy large numbers of scam tokens to maximize potential earnings – sometimes several per day.
Whitelist: A type of function that can be applied to a token, giving a specified wallet privileged access. There are many positive reasons for whitelisting, however, in a scam scenario, they are the only wallets that can sell or perform other functions.
Common Types of Scams
Honeypots:
Honeypots are the most prevalent type of cryptocurrency scam – named as such by their attractive nature that ultimately causes an investor to become ‘stuck.’ A honeypot in a technical sense is a token that can be purchased but cannot be sold. This means that once an individual invests they cannot withdraw their funds, which have been trapped within the liquidity pool and irrevocably stolen.
Developers are then able to extract these stolen funds in a variety of ways after honeypotting a token, such as by removing liquidity, minting tokens, airdropping tokens, or whitelisting wallets to sell.
Honeypots can be tricky to spot to the inexperienced trader, as the deployer will often make ‘fake’ sells on their own token with whitelisted wallets to make it appear like a legitimate investment. It is important to note that this type of scam is usually most prevalent with newly minted token launches, however, it does occasionally occur with mid-cap cryptocurrencies too.
Airdropping
Airdropping is a less overt method of scamming and can be used to fool investors into thinking a token is safe, as it can pass all other ‘sniff’ tests, (such as not being a honeypot, having locked liquidity, and an acceptable transaction tax level). Instead, the developer airdrops themselves or associated wallets, and from there can drain the funds from a token and scam investors.
For example, a developer might keep 20% of tokens, but lock liquidity and renounce the contract, making the investment appear safe. In a legitimate scenario these reserved tokens could for example be utilized for staking rewards or contests prizes. In malicious situations, however, these same tokens can be airdropped to other wallets and then sold as an indirect way of draining liquidity, even if liquidity is locked and all other safety verifications are met.
While discussing airdrops, it is worth mentioning here a completely different but potentially even more devastating airdrop scam. This is where random ‘dormant’ tokens are airdropped to an unsuspecting individual’s wallet - often with seemingly high value. Once interacted with, a back-door exploit will execute, allowing the scammer instant access to the wallet, where they can then sell all tokens and totally drain funds, in a horrific process known as ‘dusting.’ Not touching these tokens appears to (at present) mean they cannot do any damage.
Liquidity Removal:
The removal of liquidity is a somewhat overarching statement, as any type of scam where a token deployer drains liquidity (aka investor funds) can be considered ‘liquidity removal.’ In this instance, we are referring to liquidity removal as a single transaction scam, which steals all investor funds at once.
Any token that is tradeable on the blockchain has a liquidity pair on a specific DEX, typically consisting of the chain's native cryptocurrency or a stablecoin, paired with the token in question (I.E. SCAN/ETH). Token deployers typically supply the token’s liquidity, granting them privileged access over the liquidity pair. Because of this, token deployers are able to remove the liquidity in exactly the same way they added it if liquidity is not locked on a dedicated platform such as Team.Finance or Pinksale.
When liquidity is removed this is an overt action of theft – everybody’s tokens become worthless and the token is ‘dead.’
Minting Tokens:
An often malicious function, which allows the smart contract to create new tokens whenever a developer executes the process. Within a scam scenario, this effectively provides the deployer with a large quantity of free tokens while diluting every holder’s percent of supply. These tokens can then be sold to indirectly drain liquidity and steal investors' funds. While mint functions are very occasionally necessary for the functionality of certain tokens, more often than not they are a red flag when examining freshly launched micro-cap tokens.
Developer Selling:
While it is not uncommon for the developers or teams of large-cap established cryptocurrencies to sell some of their holdings as a way of earning for their hard work, doing so on a newly released micro-cap token is effectively a form of scam, due to the volatility and price impact that this can have on the chart. This is an increasingly prevalent form of scam, where no other negative functions are included in the code, but wallets connected to the developer receive the contract address early and buy large quantities at very low prices, only to sell shortly afterward.
Common Contract Functions
Key Functions:
Every smart contract has functions that can be executed by either the token’s deployer (or any other approved wallet). While the behavior of these functions and who can call them depends primarily on the code within the smart contract itself, often the name of the function can tell you what exactly the function does. Below are some common ones to keep an eye out for:
SetFees: This function dictates the percentage of tokens taken as a transaction fee on buys and sells.
Airdrop: Airdrop a number of tokens to a specified wallet.
Enable Trading: Used to open trading after liquidity has already been created, also known as “launching” the token.
Mint: Create new tokens spontaneously, typically sent to the deployer's address. This increases both the total supply and circulating supply, decreasing the value.
Max Wallet: Set the max amount of tokens a single wallet can hold.This can prevent large investors from accumulating many tokens and then dumping and destroying a chart.
Max Transaction: Set the max amount of tokens that can be bought or sold in a single transaction. Again this is useful against ‘whale’ play.
The above shows that some functions within a token’s smart token are pivotal to its operation. However, others (particularly minting) can be used to negatively exploit the contract and steal from investors, so it is crucial to pay attention to which functions have been included in a contract.
Safety Checks: The built-in CoinScan safety checks are a free feature for all users, giving them a quick and efficient insight into some of the most important variables discussed above.
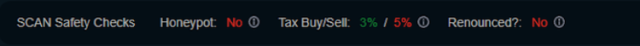
When a user inputs a token’s contract address into CoinScan, they will instantly be able to see the tax percentage, the status of liquidity lock and duration, contract renounce status, and crucially – whether it is a honeypot or not.
Is it a Honeypot?
If CoinScan reports ‘Honeypot’ then users should be wary as it means that currently purchased tokens would not be sellable. Conversely, if the token is shown as “Not a honeypot”, they can proceed with their due diligence and confirm the safety of their potential investment with more confidence. It is important to note that on new launches there are sometimes factors such as a max sell function that will trigger honeypot status even though the token is sellable. Additionally, just because a token isn’t a honeypot to begin with, developers can still manipulate certain functions built into contracts at any time to turn it into one, explained further below.
Tax Buy / Sell
While not all tokens feature a transaction tax, it is extremely common, as it helps pay for marketing and other necessary functions such as chart buybacks. It is important for users to be wary of large transaction fees as they will need to achieve at least the sum of the buy and sell fee to just break even on their investment. (For example, making 20% if there is a 10% buy and 10% sell fee). Generally speaking, the lower the transaction tax, the better. It is also important to look for extremely high sell taxes (I.E. 99%) – as it is effectively the same as a honeypot, due to exiting a position resulting in a total loss of funds.
Renounced?
The act of renouncing a contract changes the ownership to the dead address, 0x000…DEAD – a wallet that is controlled and accessible by nobody. In effect, renouncing a contract ensures that no individual – including the deployer – has access to any privileged functions. This ensures safety and token autonomy, as the functions of the smart contract can no longer be accessed or altered in any way.
While renouncing a contract is a good sign of token safety for the short term (and all other safety checks are met), it often means that the creator has short-term vision and thus is not one to be held for a long period. This is because renouncing is not a feasible option for tokens with true utility, which intend to list on exchanges (a requirement), or have any sort of dynamic development, as contract functions are necessary for longer-term evolution and adaptability.
Developer Wallet Tracker
Another great CoinScan tool that is free for all users is the Developer Wallet Tracker, which tracks the deployer’s wallet in real-time, giving users a dynamic window into what is happening behind the scenes with any token.
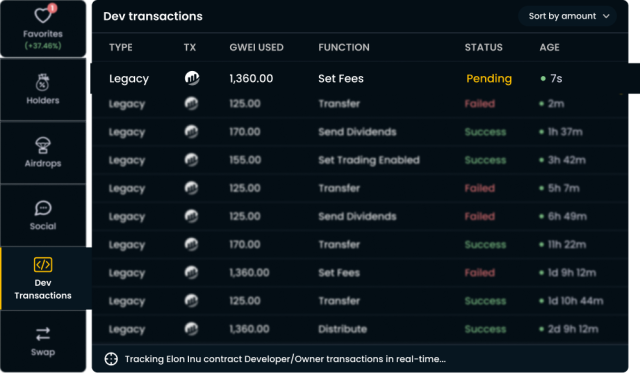
Watching the Developer Wallet Tracker on a token allows users to check transactions as they occur, and even allows them to exit tokens mid-scam before a malicious transaction is completed. (Achieved via the GWEI (gas) value of the transaction being displayed, so a quick trader can out-gas it).
Below are the key transactions that should be monitored for, in order to stay as safe as possible.
Remove Liquidity
In reference to the previous definition, our users can see a developer removing liquidity in real-time when watching the developer wallet tracker. To avoid holding a token through a liquidity removal transaction, an individual can quickly place a sell order and set a GWEI value higher than the one noted in the wallet tracker to complete their transaction before the malicious one.
Set Fees
While setting fees isn’t always a malicious action, it can be used to change a token that isn’t a honeypot, into a honeypot. In normal cases, set fee transactions are used to reduce taxes after launch for buy contests or other similar purposes. If a user sees this transaction happening and the contract is verified, they can go to etherscan and look at what values are being set. From there, they can quickly place a sell order if the values are indicative of a scam (ex: 99% sell tax).
Mint
As per the previous definition, the ability to identify a developer minting tokens in real-time is an extremely advantageous tool. If the mint transaction is believed to be of malevolent intent, placing a sell order as soon as possible typically allows the individual to exit a token before they get scammed due to the minted tokens being sold.
Transfer
While transfer transactions are typically not malicious, this is the type of transaction seen in the wallet tracker when an airdrop takes place. To decipher if the transaction is one to be concerned about, users can simply click the etherscan icon and evaluate the token amount and receiving wallet to make sure that the airdrop is not to a deployer’s wallet, nor a concerning amount of tokens.
How to exit a token when you see a pending scam transaction:
Note the GWEI of said transaction


In this example the user should use at least 1361 gwei, as the remove liquidity function was sent with 1360 gwei as seen in the first screenshot
If a user is fast enough (and prepared to pay the associated gas costs) they will successfully exit their position before the malicious transaction is completed.
Airdrop Analysis Tool
Taking a deeper dive into airdrops, it is key to identify when they might be malicious. While in some instances an Initial Coin Offering (ICO) or capital fundraising private sales require investors to get their tokens through an airdrop, in legitimate projects these are typically vested, meaning that they release slowly, over a predetermined time period. As a good rule of thumb, no single wallet should receive more than one percent of supply (>1%) without raising some serious red flags.
With the CoinScan Airdrop Analysis Tool, scrutinizing the quantity and value of airdrops is both fast and efficient. Below is an example of what to look for:
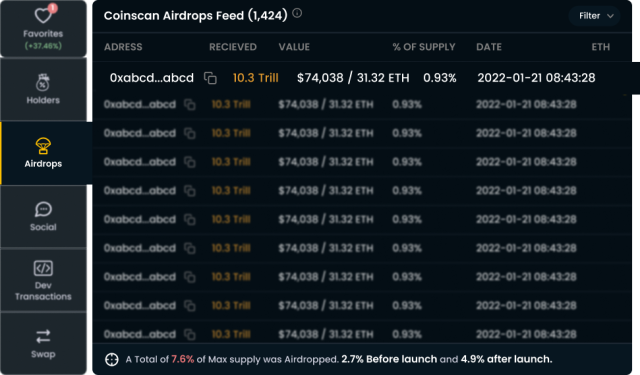
In the above proof of concept, it is easy to identify the key fundamentals of the airdrop behavior - namely which wallets received an airdrop, the date of the airdrop, what percentage of supply was airdropped, and the airdrop’s current value in both FIAT and ETH.
Breaking down the data points:
Wallet
If a user notices that a specific wallet received an unusually large amount of token supply, they can further analyze to decipher if the wallet has a connection to the deployer wallet. If it does, then it is likely indicative of an impending liquidity-draining scam.
Token Amount / Value
Identifying the token amount and ETH or FIAT value a wallet received can be very beneficial in gauging the health of a token. Unless there was an announced presale, or funds were raised for initial liquidity in other ways, seeing wallets receive large amounts of supply is a red flag.
Date
If a user notices an airdrop that causes concerns, taking a look at the date can help them identify whether the tokens were airdropped before launch, shortly after launch, or randomly throughout the token’s lifespan. If the patterns feel suspicious then again, it is typically a red flag.
Holder Analysis Tool
While every token that is tradeable has holders, wallets holding large percentages can raise concerns as (depending on the tokens liquidity and therefore price volatility), an individual holder could sell their entire position and cause the token value to crash. In fact, malicious investors often do this to incite sell-offs and then buy in again at low price points, in a rinse and repeat cycle, known as ‘whale play.’
The CoinScan Holder Analysis Tool enables users to easily gauge a token’s distribution and gain an insight into exactly how holders are behaving, such as what percentages have been sold for and at what value. This level of analysis can be extremely beneficial before investing in a chosen token, as users can identify whether top holders will provide reliable sell pressure resistance or are instead consistently selling their tokens, making a downtrend inevitable. While this is not an exact science, such metrics give users a keen advantage over others in navigating the DeFi space.

Stay Safe
Scams are becoming more prevalent in the cryptocurrency space and wise investments are key to staying safe and avoiding becoming the target of such manipulations. Indeed, the features highlighted above are the tip of the iceberg on how CoinScan can benefit users and help them invest strategically. Learning how to effectively utilize these essential tools to avoid scams and solidify investment sentiments gives users an edge that simply isn’t available elsewhere. Of course more experienced traders can manually accrue some of the data points we provide, although it is far less streamlined and user-friendly, meaning loss of time – and in cryptocurrency, time is literally money!
The team has a lot more coming behind the scenes at CoinScan so make sure to join our welcoming SCANFAM at the official Telegram channel here. Also signing up for our Newsletter is a great way to stay on trend with all new developments and breaking market news.
Stay safe out there Scanners!
About the Author
Denis is an avid Crypto and Blockchain Enthusiast. Having founded a crypto marketing company in 2020, and being full time in the space for over 5 years now, Denis is a big believer in the future of web3 and the potential it has to change the world.


